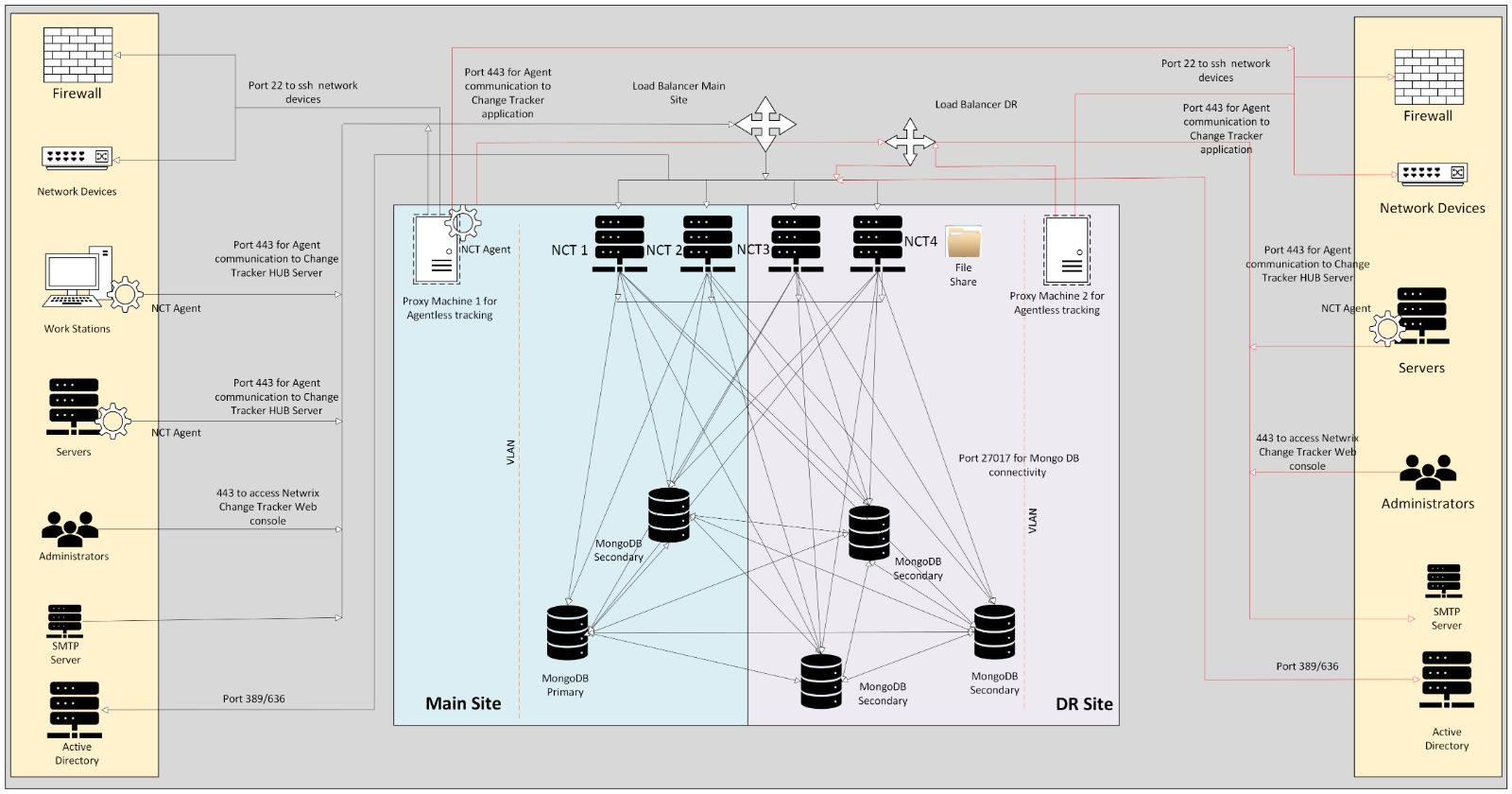
NCT Multi node setup Distributed architecture
Overview
Netwrix Change Tracker is a FIM solution designed to monitor and secure an organization’s critical IT infrastructure, including operating systems, network devices, containers, and databases. It strengthens security and helps achieve compliance by enforcing configuration baselines on critical systems to prevent configuration drift. It also supports regulatory frameworks like PCI DSS, HIPAA, NIST, and SWIFT to help automate auditing.
Client requirements
- FIM solution with a business continuity plan.
- Custom tracking and compliance aligned to KSA Security guidelines.
- Onsite deployment and training.
Roles and Responsibilities
Architecture & Solution Design
- Designed a custom distributed multi-node architecture tailored to compliance and HA requirements.
- Built the full solution in a lab environment to perform end-to-end testing and validate assumptions before deployment.
- Prototyped with SKUDONet HA load balancer and NGINX to evaluate traffic distribution, redundancy, and health checks.
- Prepared prerequisites, including network diagrams, system requirements, and firewall matrix.
Environment Validation
- Validated OS configurations, SSL trust chain, firewall dependencies, service accounts, and clustering readiness.
- Simulated Cisco routers and switches in GNS3 for FIM testing; validated polling frequency for change tracking.
- Tested network paths to confirm stable communication across NCT nodes and MongoDB cluster members.
MongoDB Cluster research, design & security hardening
- Researched MongoDB replica set clustering to support the distributed architecture.
- Configured SHA‑256 based x.509 certificates to secure intra‑cluster communication.
- Tested failover behavior, election timing, data synchronization, and resilience.
Deployment & Configuration
- Installed and configured all NCT components across distributed nodes following vendor best practices.
- Implemented custom tracking profiles and compliance baselines aligned with KSA Security Guidelines.
- Fine‑tuned monitoring policies to reduce false positives and improve alert fidelity.
- Integrated NCT with ITSM workflows to match planned changes against change requests automatically.
- Improved security posture by configuring baseline templates, increasing the security score by 20%.
High availability automation (custom IIS restart script)
To address the lack of native HA, implemented a PowerShell‑based IIS restart script to maintain application availability across 4 nodes.
- Used response headers and backend server checks via the load balancer URL to detect the active node.
- Restarted IIS only on secondary nodes to maintain availability.
- Scheduled the script via Task Scheduler every 30 minutes to keep cache warm.
Testing & Failover verification
- Performed controlled failover simulations (application and database layers) to validate continuity and zero‑loss recovery.
- Executed performance and functional testing to confirm tracking accuracy, compliance policies, and HA stability.
Documentation & knowledge transfer
- Produced documentation: As‑Is, failover runbooks, and administrative guides.
- Delivered onsite training covering operations, troubleshooting, and policy management.
Impact
- Improved organizational compliance by 23%.
- Reduced response time for IT and security teams to investigate and remediate incidents.
- Enabled forensic‑level investigations (who, what, when, where changes occurred).
- Achieved database and application HA with reliable failover, ensuring business continuity.
Tools & technologies used
| Tools | Platform |
|---|---|
| Operating System | Windows Server 2019 & 2022, RHEL 7 & 8 |
| Web Services | IIS 10 |
| Database | MongoDB 7.x |
| Network simulator | GNS3 |
| Load Balancer | SKUDONet & NGINX |
| Firewall | pfSense 2.x |